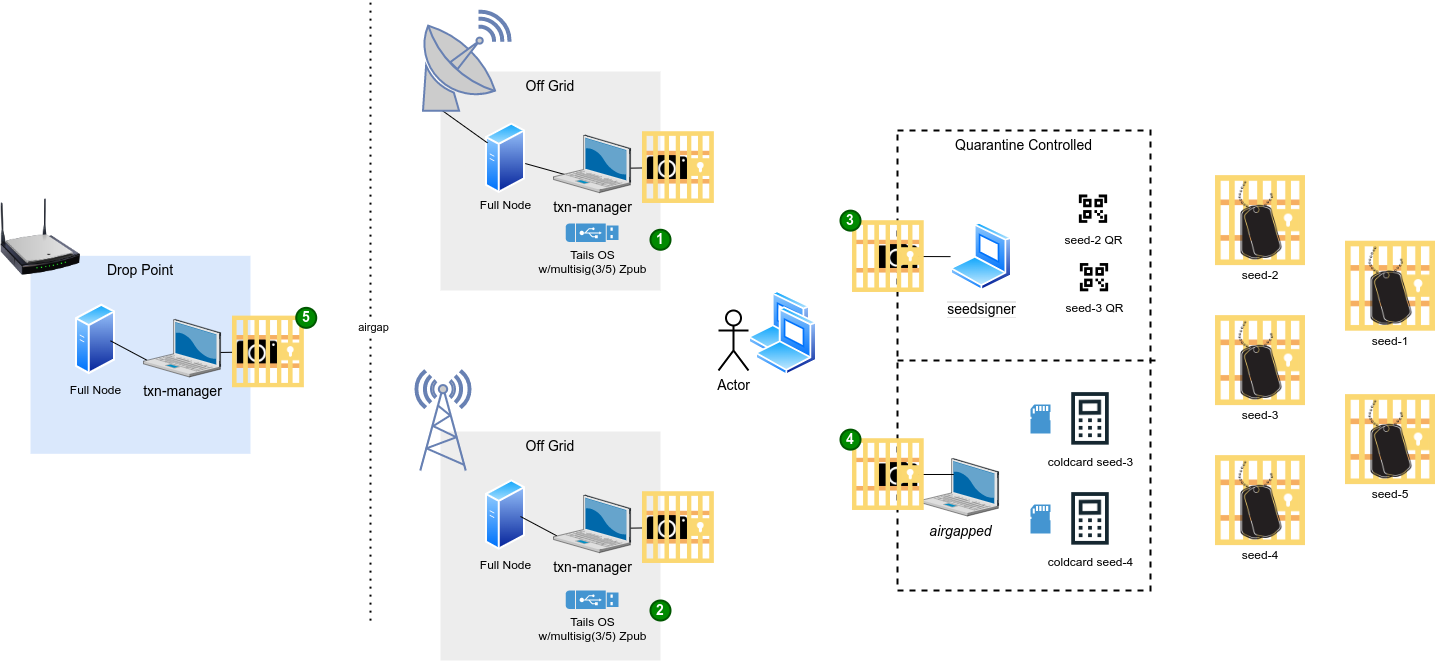
Appendix: Ludicrous Protocol¶
This protocol delivers an ultra-secure 3-of-5 multisig Bitcoin self-custody system using five different Signing-Devices: three SeedSigners and two Coldcard Qs (one per seed). It leverages an expanded airgap quarantine covering both DMZs, redundant receive-only full nodes (RF and satellite), metal seed backups, geographically distributed key signing, and stringent quarantine rules to provide unparalleled protection. By using distinct devices per seed, redundant systems, and advanced countermeasures, this protocol achieves Level 12 security, ensuring resilience against state-level threats.
Receive-only (e.g., satellite) nodes with geographically distributed key signing.
Secure Environment and Countermeasures¶
To safeguard against advanced threats, all QR code transfers must be conducted in secure, geographically distributed environments with the following countermeasures:
- Geographical Distribution: Store each Signing-Device in a unique, secure location (e.g., vaults, Faraday-protected rooms).
- Expanded Airgap: The airgap extends across both DMZs, isolating all critical operations from network threats.
- Secure Spaces: Each location must be a private, controlled room with no windows or cameras.
- Shielded Environments: Use Faraday cages or shielded rooms to block electromagnetic emissions.
- Privacy Filters: Polarized screen protectors on all device screens to prevent optical eavesdropping.
- White Noise Generators: To mask acoustic signals during device operation (preferably non-electronic).
- Privacy Enclosures: Lightproof booths for QR scanning to shield from external observation.
- Camera Blockers: Covers or tape to disable cameras on the Transaction-Managers when not in use.
- Tamper-Evident Seals: Applied to Signing-Devices when stored to detect unauthorized access.
Quarantine Rules¶
To achieve the highest level of security for your Bitcoin self-custody, follow these rules as a concise, numbered checklist. These rules extend the original Level-5 quarantine to include advanced countermeasures (suitable for the "Ludicrous" protocol), ensuring protection against physical, digital, and human threats.
Adhere to these rules without exception during any session involving seeds or transaction signing.
-
Limit data transfers to QR codes only: No physical media (e.g., USB, MicroSD) is allowed across the quarantine. Rationale: Prevents malware vectors and enforces manual verification.
-
Expose seed phrases only on the Signing-Device: Never display, write, or input seeds on any other component. Rationale: Isolates the most critical secret to one tamper-resistant device.
-
Stow all smartphones and personal electronics in Faraday bags outside the room: Power them off first. Rationale: Blocks remote activation of microphones, cameras, or transmitters.
-
Ban all electronic devices near the Signing-Device; use non-electronic white noise generators and privacy enclosures: Exclude any potential sources of acoustic or electromagnetic leaks. Rationale: Mitigates side-channel attacks (e.g., audio or EM data exfiltration).
-
Ensure complete physical privacy with secure spaces and privacy filters: Use a locked room with no windows or cameras, and apply polarized screen protectors to all devices. Rationale: Prevents optical surveillance and physical access.
-
Sanitize and verify all tools pre-session: Check software/firmware signatures, verify tamper-evident seals on Signing-Devices, and test tool integrity. Rationale: Counters supply-chain attacks and pre-installed malware.
-
Distribute and redundantly store components geographically with tamper-evident seals: Store Signing-Devices in separate, secure locations. Rationale: Ensures resilience against localized physical attacks (e.g., theft, fire).
-
Use receive-only full nodes (RF and satellite) for blockchain data: Utilize RF and satellite-based nodes to receive tamper-proof data without transmitting. Rationale: Maintains privacy and resilience against network censorship.
-
Employ redundant Transaction-Managers on isolated networks: Use two Transaction-Managers, each linked to a separate receive-only node. Rationale: Provides redundancy and independent cryptographic verification of all steps.
-
Implement an expanded airgap covering the receive-only full nodes and Transaction-Managers: Isolate all critical operations from network threats. Rationale: Protects against all network-based attacks.
-
Utilize a secure drop point for broadcasting signed transactions: Designate a single physically secure, monitored location, used only for broadcasting signed transactions. Rationale: Ensures secure handling of transaction broadcasting.
-
Coordinate signing sessions securely across geographically distributed locations: Follow strict procedures for QR transfers and quarantine rules at each site. Rationale: Maintains security in a distributed setup.
These rules, when followed meticulously, create a fortress-like barrier around your Bitcoin, making unauthorized access or compromise exponentially difficult -- even for advanced adversaries.
Setup¶
Establish your 3-of-5 multisig wallet with five seeds created on dedicated Signing-Devices (one device per seed). Conduct this in secluded, secure settings across multiple locations, maintaining airgaps and quarantine procedures.
1. Prepare Secure Environments
- Acquire five Signing-Devices: three SeedSigners and two Coldcard Qs, each for one seed.
- Set up three secure spaces for QR transfers in geographically distributed locations: private rooms with no windows or cameras, each equipped with a physical and electronic countermeasures, such as non-electronic white noise generators, and privacy enclosures.
- Install privacy filters on all Signing-Device and Transaction-Manager screens.
- Prepare camera blockers for the Transaction-Managers.
- Obtain tamper-evident seals for the Signing-Devices.
- Assemble two Transaction-Managers (Tails OS with persistent storage) within the airgap, each linked to a receive-only full node: e.g., one RF and one satellite.
- Install Sparrow and detection tools (for data exfil attacks like Dark Skippy) on both Transaction-Managers' persistent storage.
- Authenticate and update software and firmware for all devices.
- Designate a secure drop point for broadcasting signed transactions, with a full node and a Transaction-Manager running Tail OS and no persistent storage. This drop point will be used only for broadcasting signed transactions (everything else will happen within the quarantined airgap).
2. Set Up Receive-Only Full Nodes
- Satellite-Based Full Node:
- Set up a receive-only full node using Blockstream's satellite service to receive blockchain data without internet.
- Follow the setup guide at blockstream.com/satellite.
- RF-Based Full Node:
- Set up a second receive-only full node using an RF source for decentralized blockchain data reception.
- Use a reliable guide like the RTL-SDR Bitcoin Blockchain Guide for setup instructions.
- Ensure both nodes are configured as receive-only to maintain the airgap and prevent any outbound data transmission.
3. Generate Seeds
- Activate each airgapped Signing-Device in its respective secure location, one at a time.
- Generate a seed on each device (SeedSigner: Settings > Seeds > Generate Seed with dice; Coldcard Q: generate with dice). Ensure privacy filters are installed to protect displays.
- Jot the seed phrase on paper temporarily for confirmation.
- Validate the seed on the device display.
- Save as QR (SeedSigner: Export Seed QR; Coldcard Q: Export Seed QR).
- Repeat for all five seeds, powering off devices between steps. Label clearly (e.g., "Signing-Device-1", "Signing-Device-2").
4. Backup to Metal
- Stamp each seed onto durable metal backups.
- Cross-verify against the paper note.
- Incinerate the paper note.
- Store backups in distinct, secure sites with tamper-evident seals.
5. Export ZPUBs to Transaction-Managers
- On each Signing-Device, load its seed and export ZPUB (SeedSigner: Export XPUB > Multisig; Coldcard Q: Export Wallet > Multisig).
- Following secure QR transfer procedures, convey ZPUBs via QR to both Transaction-Managers within the airgap.
- Integrate ZPUBs into Sparrow on both Transaction-Managers for a 3-of-5 multisig watch-only wallet.
6. Validate Addresses for Future Deposits
- Produce receive addresses in Sparrow on both Transaction-Managers.
- Following secure QR transfer procedures, relay addresses via QR to each Signing-Device for verification.
- Confirm derivation from ZPUB on each device.
7. Test Setup with Small Transaction
- Transfer a small Bitcoin amount following the Deposit procedure.
- Observe confirmation on both receive-only full nodes.
- Transfer some Bitcoin following the Withdrawal procedure (sign with three devices from different locations).
- Validate the workflow and record issues.
Deposit¶
Receive Bitcoin using unique, verified addresses confirmed through both receive-only full nodes.
1. Generate Receive Address
- Start Sparrow on both Transaction-Managers within the airgap.
- Generate a new receive address from the multisig descriptor and ensure it matches on both.
2. Verify Address on Airgapped Device
Optional -- used when no pre-verified address is available. 1. Following secure QR transfer procedures, send address data via QR to at least three Signing-Devices. 2. Confirm ZPUB derivation on each device.
3. Share Address with Sender
- Deliver the verified address securely.
- Await the transaction in Sparrow on both Transaction-Managers.
4. Monitor Incoming Transaction
- Check the transaction on both receive-only full nodes or Sparrow on both Transaction-Managers.
- Await confirmations and ensure consistency across nodes.
Withdrawal¶
Spend Bitcoin via multisig signing with three Signing-Devices from different locations.
1. Create Unsigned Transaction
- Open Sparrow on both Transaction-Managers within the airgap.
- Select UTXOs, define recipient and amount.
- Export the PSBT as QR, ensuring both Transaction-Managers generate identical PSBTs.
2. Transfer Unsigned Transaction to Airgapped Device
- Following secure QR transfer procedures, convey the PSBT via QR to each of the three Signing-Devices in their respective locations.
- Load the PSBT on each device without signing.
3. Sign Transaction
- On each of the three Signing-Devices, load the assigned seed and generate a partial signature.
- Following secure QR transfer procedures, export the partial PSBT as QR to both Transaction-Managers.
- Power off devices to clear memory.
4. Combine Signatures and Finalize Transaction
- Merge the three partial signatures in Sparrow on both Transaction-Managers.
- Validate the finalized transaction on both systems.
5. Inspect Transaction
- Use detection tools (for Dark Skippy style attacks) on both Transaction-Managers to scan for anomalies.
- If issues are detected, abort and investigate.
6. Broadcast Signed Transaction
- Transfer the signed transaction from the airgap to the secure drop point.
- Broadcast via the online Transaction-Manager at the drop point.
- Monitor confirmations on both receive-only full nodes within the airgap.
Check Balance¶
View balances without keys, using both receive-only full nodes.
1. Sync Watch-Only Wallet
- Start Sparrow on both Transaction-Managers within the airgap.
- Connect to their respective receive-only full nodes and sync.
2. Query Balance for Multisig Addresses
- Check the balance in Sparrow on both Transaction-Managers and confirm consistency.
Recovery¶
Restore from backups if keys or devices are lost. Use new Signing-Devices for multiple recoveries.
1. Identify the Issue
- Determine the recovery type (e.g., lost device).
- Retrieve metal backups from secure sites.
2. Retrieve Backups
- Access backups from their secure locations.
- Check tamper seals.
3. Restore Keys on New Signing-Device
- Input the backup seed on a new Signing-Device with privacy filters installed in a secure location.
- Validate the restored wallet.
4. Rebuild Multisig Wallet Descriptor
- Following secure QR transfer procedures, export ZPUBs to both Transaction-Managers.
- Recreate the multisig descriptor in Sparrow on both systems.
5. Test Recovery with Small Amount
- Perform a test transaction to confirm functionality.
Maintenance¶
Sustain protocol integrity with regular tasks across all locations.
1. Verify Metal Backups
- Inspect tamper seals and metal condition at each secure site.
- Test seeds on Signing-Devices.
2. Update Software and Firmware
- Check for updates and verify signatures.
- Update firmware in an airgapped environment at each location.
3. Run Full Node Health Checks
- Ensure both receive-only full nodes are synced and consistent.
4. Simulate Full Protocol Run
- Test the entire protocol with small amounts, signing from multiple locations.
- Verify the secure environments and countermeasures.
5. Check Secure Environments
- Ensure shielded rooms, privacy filters, and white noise generators are functional at all locations.
- Inspect tamper-evident seals on Signing-Devices.
- Verify the integrity of the receive-only nodes and their connections.
This protocol achieves Level 12 security by integrating geographically distributed key signing, an expanded airgap covering redundant DMZs, receive-only nodes (RF and satellite), redundant Transaction-Managers, and a secure drop point, all to protect a 3-of-5 multisig setup, ensuring protection against the most sophisticated threats.